Recent trends indicate a new tactic employed by contact form spammers: exploiting Cloudflare WARP. This free VPN, which utilizes Cloudflare’s range of IPs, offers spammers an ingenious loophole. Given that these IPs are frequently whitelisted by numerous web services, spammers leveraging Cloudflare WARP can easily bypass sites that depend on Cloudflare for bot protection.
Fortunately, Cloudflare’s IP addresses are public information. This makes it relatively straightforward to set up filters based on Cloudflare’s public CIDR range. In this guide, we’ll focus on blocking spammers who misuse Cloudflare WARP for sending POST HTTP requests, which is required for form submission.
Our aim is to strike a balance: while we want to block malicious activity, we also don’t want to prevent genuine Cloudflare WARP users from accessing our site. By following this guide, you’ll be able to shield your site from spammers while ensuring legitimate visitors can still reach out and engage with you through other channels.
Setting Up WAF to Shield Against Spammers Utilizing Cloudflare WARP
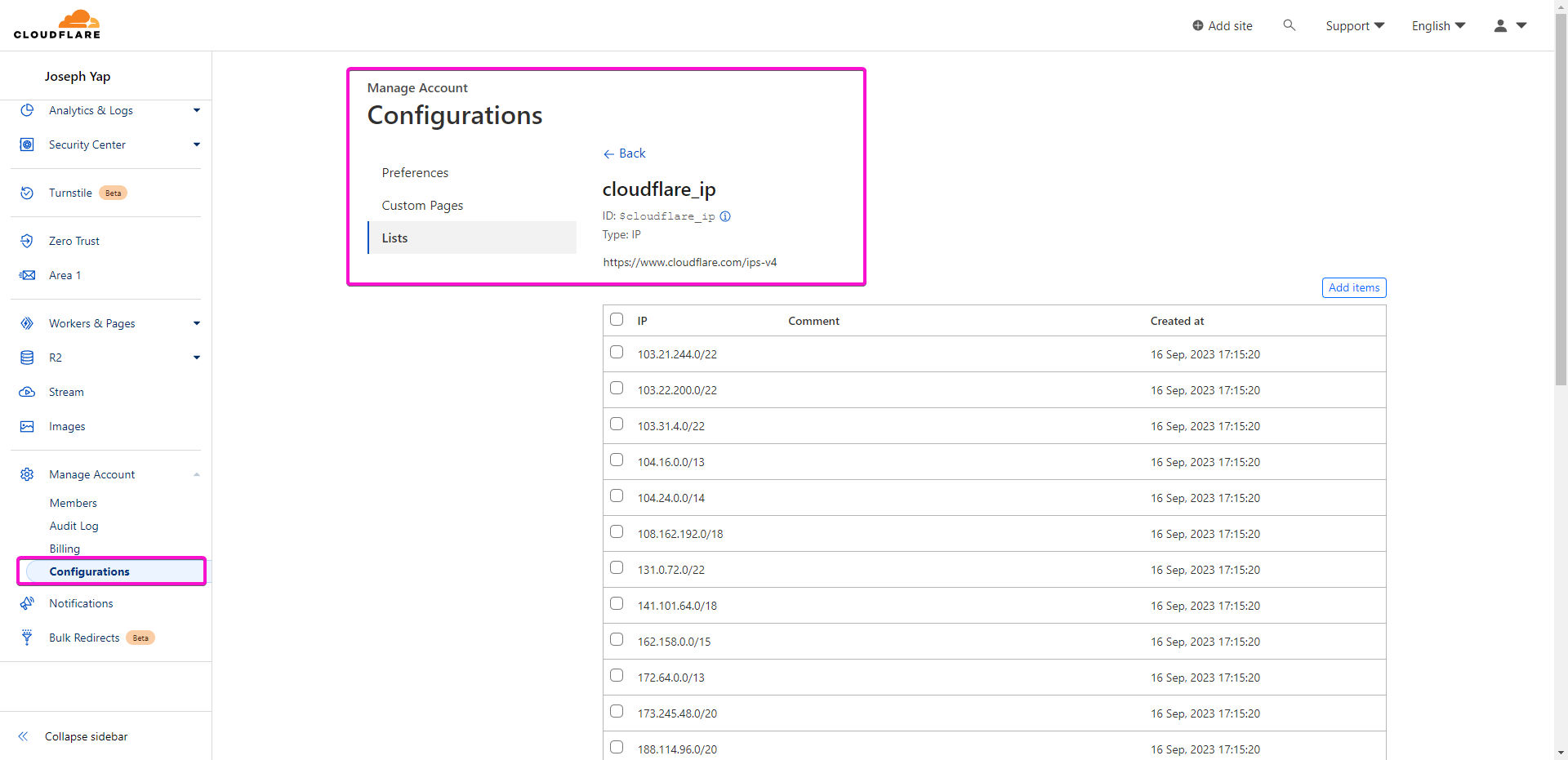
The first step towards fortifying your website against these spammers is to curate a list of all Cloudflare IPs. This list will serve as the foundation for your WAF (Web Application Firewall) rules. To achieve this, we can simply use all the publicly available Cloudflare IPs.
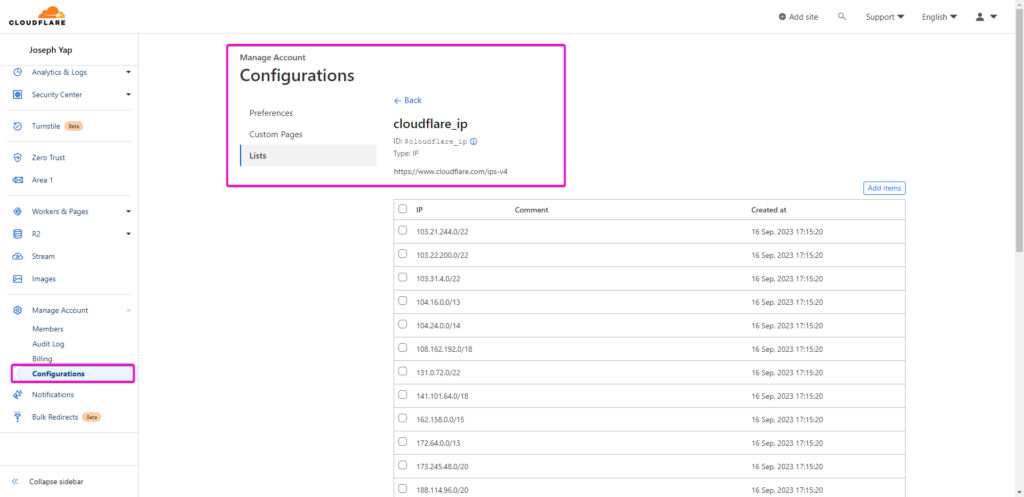
Once you’ve compiled your list, proceed to the website you intend to protect. Navigate to its WAF settings. Here, you’ll be crafting rules that employ both your Cloudflare IP list and a request method filter.
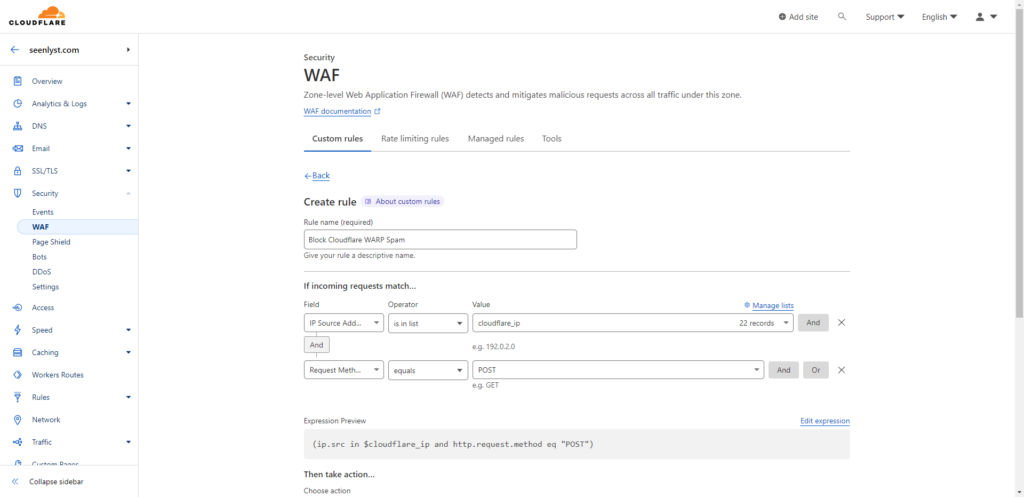
If your website hosts genuine users via Cloudflare WARP or includes functions/plugins dependent on POST requests, you might want to be more discerning with your filters. In such scenarios, incorporating a URI filter will grant you more specificity and accuracy in targeting spammers.
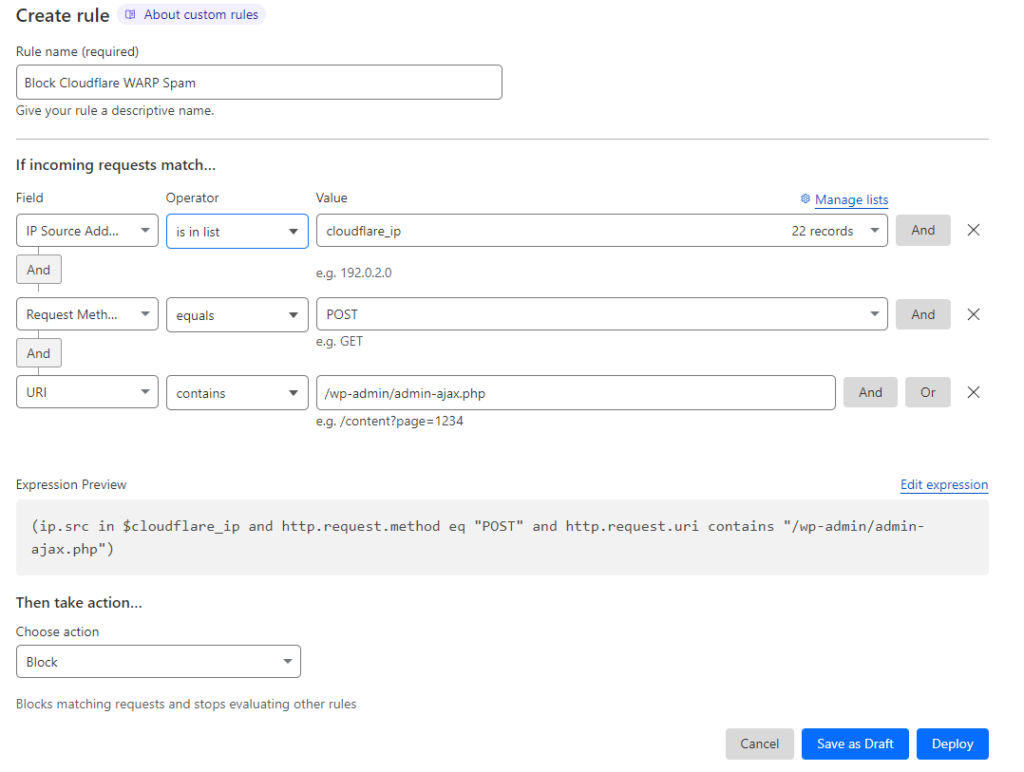
As a concluding step, ensure the action is set to ‘block’ before finalizing and deploying your rules. This guarantees the undesired traffic from the specified IP range gets stopped in its tracks.
Ensuring Your WAF Rule Functions As Expected
To ascertain that your WAF rule is functioning properly, there are two methods of verification:
Manual IP Test: Start by adding your own IP address to the list. Subsequently, attempt to use the contact form. If your rule is correctly configured, a POST request to submit the contact form will trigger a 403 response.
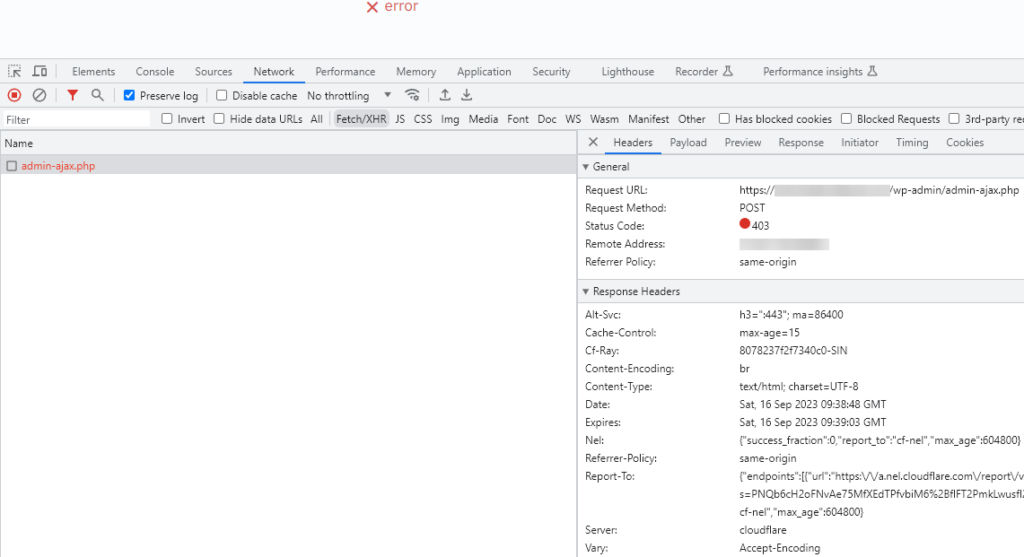
Using Cloudflare WARP: You can also test the rule by accessing your site via Cloudflare WARP and trying to submit a POST request through the contact form. However, remember: if Cloudflare assigns you an IPv6 address, the WAF rule might not intercept it. This is due to the list’s inability to handle IPv6 addresses broader than /64. That said, our observations indicate that the majority of spam originates from IPv4 addresses via Cloudflare WARP, so this limitation might not pose a significant concern currently.
Opting to Block All Traffic via Cloudflare WARP
Certain WordPress site owners have reported XML-RPC attacks traced back to Cloudflare WARP, suggesting that the free VPN service might be abused by a spectrum of spammers and malicious actors.
If you are confident that you don’t have any legitimate users accessing your site via Cloudflare WARP, you can streamline your WAF rule. Instead of applying multiple filters, simply block any visitor whose IP corresponds with the Cloudflare list. This approach offers a more robust defense against potential threats from Cloudflare WARP users.